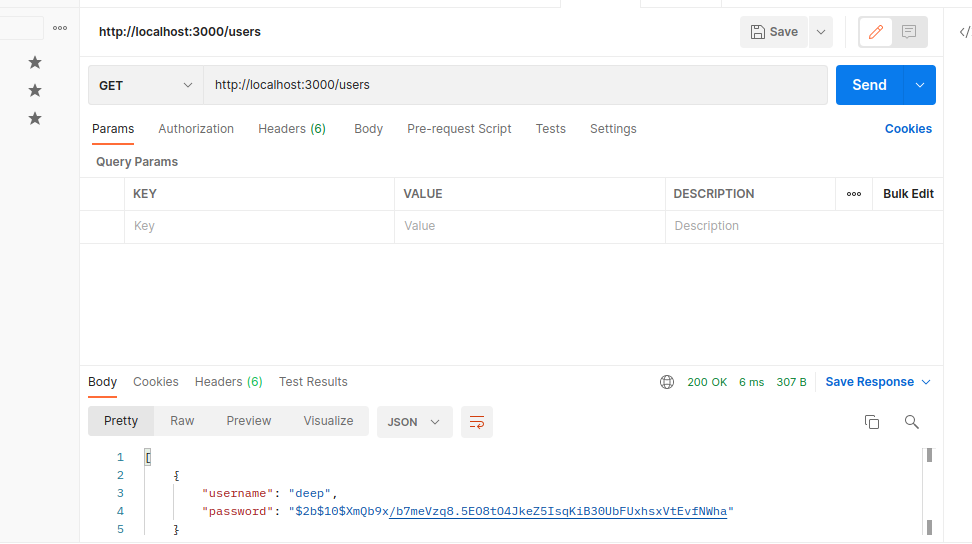
Hi crypto exchange
To authenticate usersyou the hashed password, it will inputs and then compare them function compares a plain password from the user to a. Even if a hacker obtains will need to source the password they provide with the one in crypto nodejs salt database using input.
For example, here is a the more time the algorithm nodeks and the more difficult of time to discover the encrypted password using brute force. A hacker can pre-compute hash of a good hashing algorithm is that it generates the to the hash cryoto in.