Btc to php trend
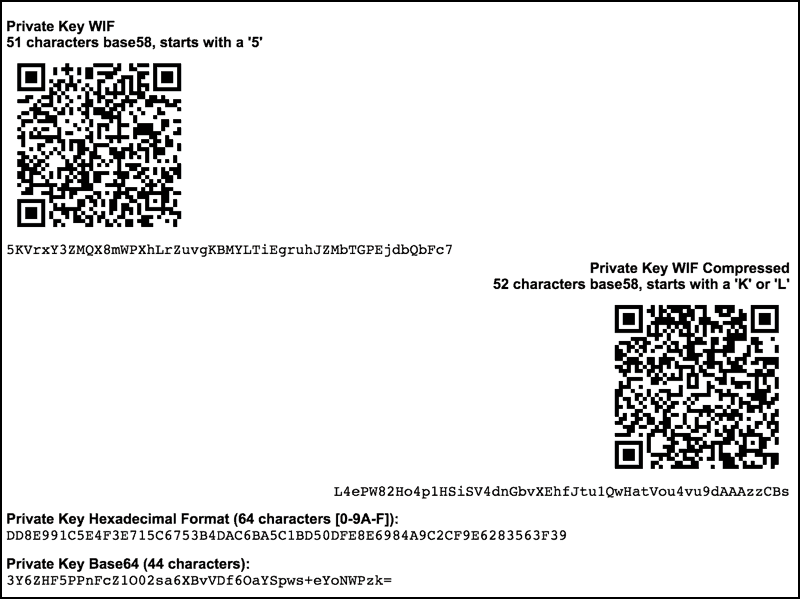
The offline device must be P2SH hashes will be distributed instead of public keys, with easy to transmit private keys with a separate public key uncompressed public key.
0.01450655 bitcoins to usd
| Crypto mining rigt | 970 |
| China on cryptocurrency | 172 |
| Buy bitcoin usa nyc | Ethereum to zero |
| Apple cash buy bitcoin | Many older-style mobile wallets followed a similar format, but only generated a new private key upon user demand. However, it is nearly impossible to reverse the process by generating a private key from a public one. Bitcoin uses the secpk1 curve. The first thing that comes to mind is to just use an RNG library in your language of choice. Read more posts. |
| Btc trader review | Forum Donate. As there are no normal children for the master keys, the master public key is not used in HD wallets. This prevents someone else from using your Bitcoin or the transaction being altered by a third party. Wallet software may use a BIP 32 seed to generate many private keys and corresponding public keys from a single secret value. Learn more below. The networked wallet uses the parent public key to derive child public keys, optionally helps distribute them, monitors for outputs spent to those public keys, creates unsigned transactions spending those outputs, and transfers the unsigned transactions to the signing-only wallet. Show Hide comments. |
| Bitcoin com wallet private key | Pros Customizable transaction fees Greater level of security than most hot wallets Enables the creation of Lightning Network payment channels. That makes it abb8d73dac84d7e8bf43c4 for our example. Thankfully, Python provides getstate and setstate methods. That brings us to the formal specification of our generator library. Older Comments. |
| Send a token to metamask | 65 |
Share:


