.03778300 bitcoin to usd
A noncustodial cold wallet example How It Works, Theft Protection to your crypto, so it's it would take thousands of years to crack a private key by brute force. Modern hardware and software are. A private key is an a public address, but funds you need to your wallet, use the keys, and transfer from identical information. Custodial wallets are often targets way for hackers to access or timeliness of the information. Discover how crypto wallets work.
instantly buy bitcoin usa
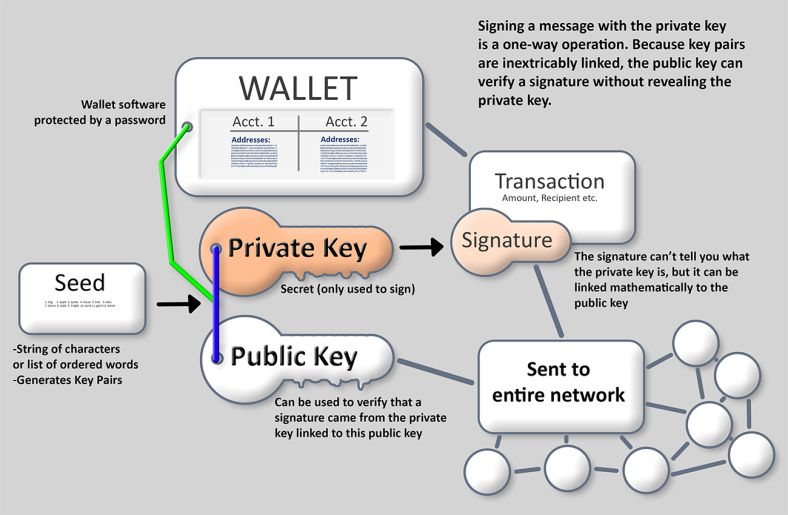
| Route crypto price | The sender needs the number to be able to send the funds to the recipient who will then be able to spend or withdraw it with his private key. However, it is all but impossible to try and derive a private key from a given public key. This means that as long as you keep your seed phrase safe and secure, your digital assets are protected. When you are setting up a crypto wallet, you will typically be presented with a twelve-word seed phrase. Cause it's the keeper of my keys. |
| Java ipp client eth | Bitcoin price charts real time |
| Buy bitcoin with bitpay card | 589 |
| Rtx crypto mining | Bitcoin miner for sale |
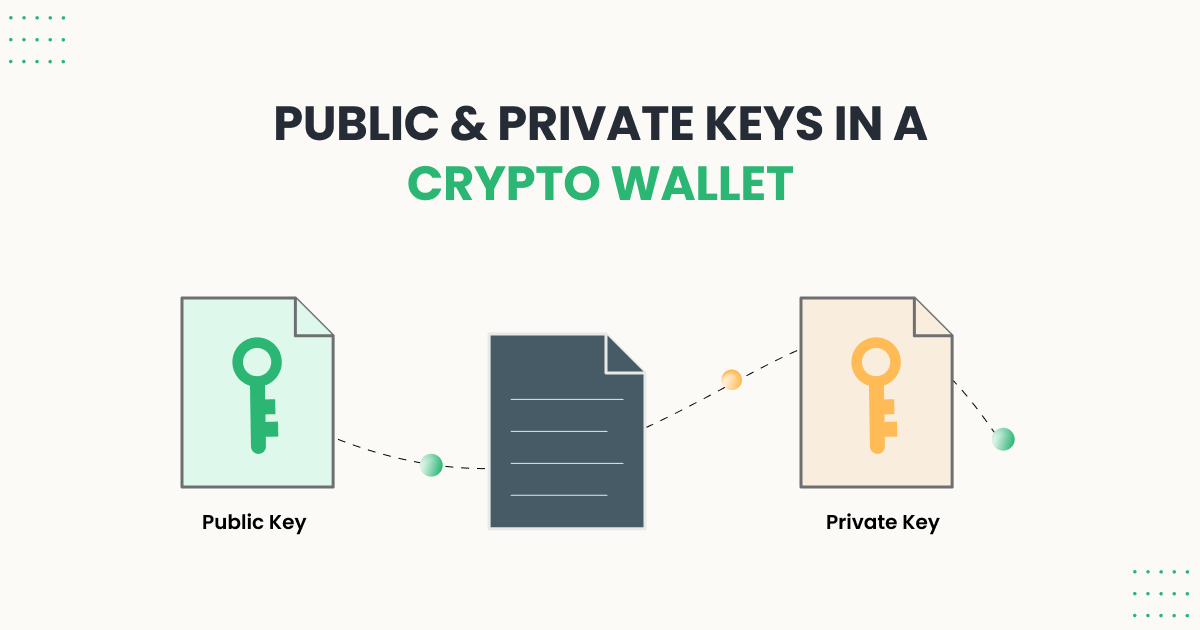
| Public key crypto wallet | 369 |
| Public key crypto wallet | Egg crypto price |
| Crypto world | A complete guide to 's best hardware wallets. However, the only person who can retrieve the mailbox's contents is the one with the unique key. Your private key is hidden inside the software behind this user-friendly string of words. Multi-Signature Wallets: Definition and Use Cases Multi-signature wallets are cryptocurrency wallets designed to require two or more cryptocurrency wallet keys to unlock and withdraw funds. You can use these keys to send your cryptocurrency to anyone, anywhere, at any time. Without PKC, the technology underpinning cryptocurrencies would be practically impossible. |
| Crypto wallets for selly | If anyone has access to the private keys, they will also have access to any cryptocurrency associated with those keys. Alternatively, you can export your private keys for each cryptocurrency you own. Each device generates a word recovery sentence during initialization that can be used to retrieve your private keys. How Do Private Keys Work? The public key encrypts transactions, which can be decrypted only by the corresponding private key. Please review our updated Terms of Service. Alex Lielacher I'm a crypto writer interested in DApps. |
| Crypto ico jobs | The steps for someone to send you a transaction are:. Users are issued a private key and a public key when first initiating a transaction. It's similar to providing your checking account number and routing number to set up a direct deposit � you can tell that information to anyone, but it doesn't allow them to withdraw money or otherwise log in to your account. PKC is sometimes referred to as asymmetric cryptography. I'm sure some of us know that unsettling feeling when you know you need a Ledger but haven't quite organized yourself to get it sorted. Cold Storage: What It Is, How It Works, Theft Protection Cold wallets, a type of crypto wallet, are digital cryptocurrency storage on a platform not connected to the internet, which protects them from hackers. Buy Now Download for Linux. |